metadata-support - [Metadata-Support] Reg: Shibboleth Integration Unable to locate metadata for identity provider Issue.
Subject: InCommon metadata support
List archive
[Metadata-Support] Reg: Shibboleth Integration Unable to locate metadata for identity provider Issue.
Chronological Thread
- From: PraveenKumar Dokula <>
- To: "" <>
- Cc: Sundar Anupindi <>, Umesh Ganti <>, suryateja rani <>
- Subject: [Metadata-Support] Reg: Shibboleth Integration Unable to locate metadata for identity provider Issue.
- Date: Tue, 19 Mar 2019 14:27:44 +0000
Hi InCommon Team,
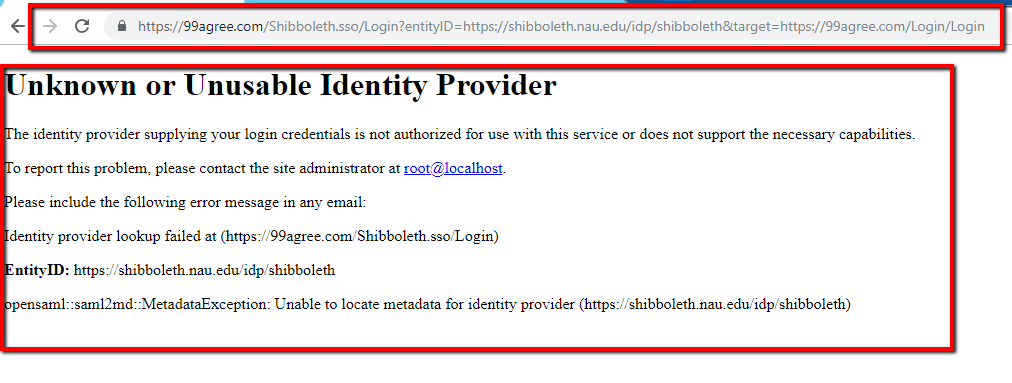
We are trying to configure the metadata for an identity provider (https://shibboleth.nau.edu/idp/shibboleth) but we are getting the issue like:
Unknown or Unusable Identity Provider
Identity provider lookup failed at (https://99agree.com/Shibboleth.sso/Login)
EntityID: https://shibboleth.nau.edu/idp/shibboleth
opensaml::saml2md::MetadataException: Unable to locate metadata for identity provider (https://shibboleth.nau.edu/idp/shibboleth).
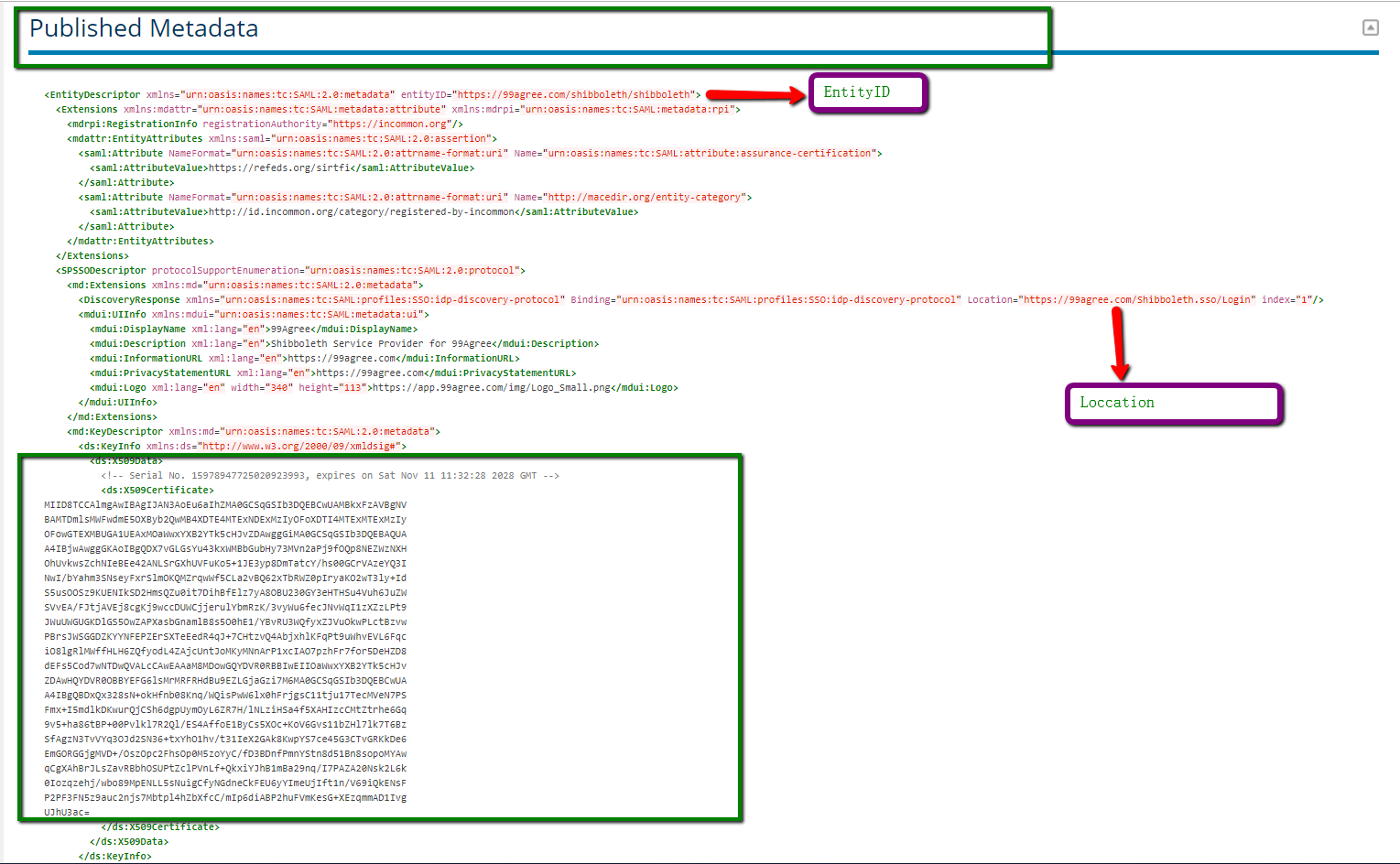
My Service provider Entity:
https://99agree.com/shibboleth/shibboleth
Metdatadata Identity provider:
https://shibboleth.nau.edu/idp/shibboleth
Please find the attachments of https://99agree.com/Shibboleth.sso Status, Metadata, Shibboleth2.xml and please find screenshots below for InCommon
Published Metadata also:
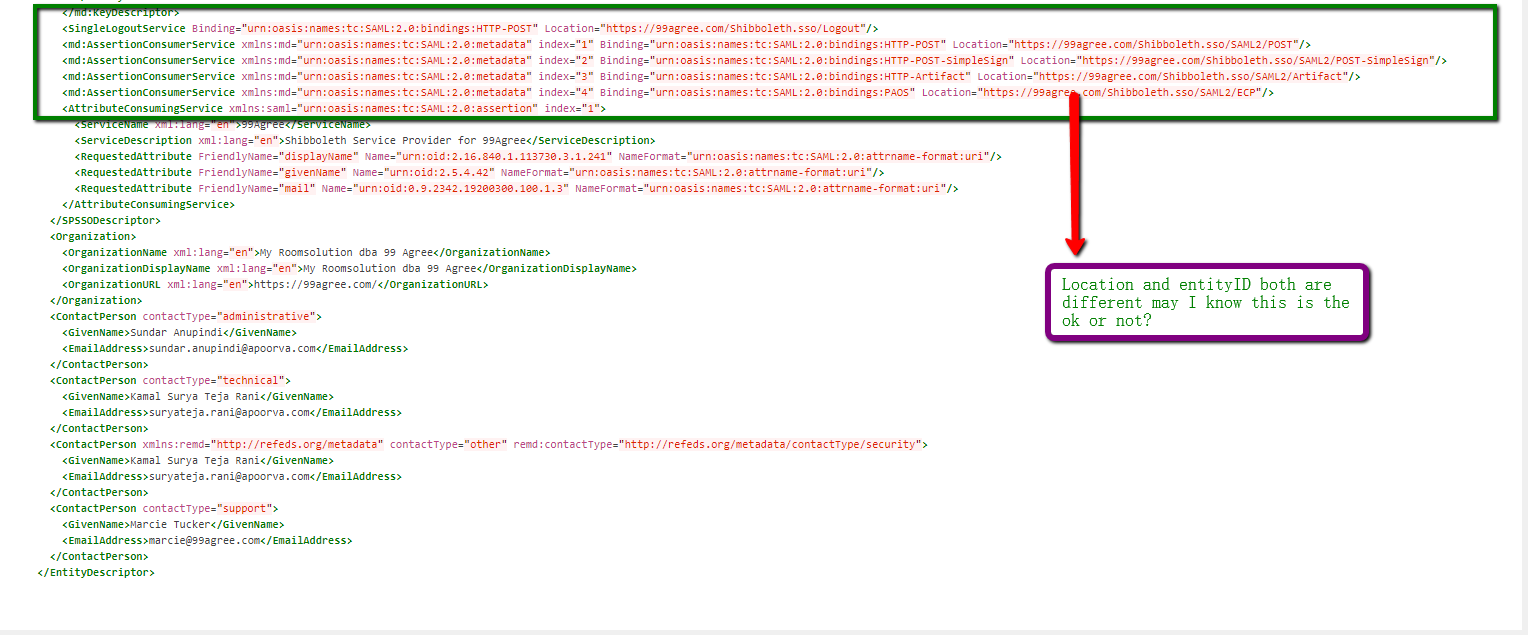
Please help us regarding this issue or guide if we are doing anything wrong, Thanking you.
Regards,
Praveenkumar D.
Attachment:
99AgreeProdMetadata
Description: 99AgreeProdMetadata
Attachment:
Shibboleth.sso_Status.png
Description: Shibboleth.sso_Status.png
<SPConfig xmlns="urn:mace:shibboleth:3.0:native:sp:config"
xmlns:conf="urn:mace:shibboleth:3.0:native:sp:config"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata"
clockSkew="180">
<InProcess logger="native.logger">
<ISAPI normalizeRequest="true" safeHeaderNames="true">
<!-- <Site id="1" name="sp.example.org"/> -->
<Site id="5" name="99agree.com" scheme="https" port="443"/>
</ISAPI>
</InProcess>
<RequestMapper type="Native">
<RequestMap>
<Host name="99agree.com">
<Path name="secure" authType="shibboleth" requireSession="true"/>
</Host>
</RequestMap>
</RequestMapper>
<ApplicationDefaults entityID="https://99agree.com/shibboleth/shibboleth";>
<!--
Controls session lifetimes, address checks, cookie handling, and the protocol handlers.
You MUST supply an effectively unique handlerURL value for each of your applications.
The value defaults to /Shibboleth.sso, and should be a relative path, with the SP computing
a relative value based on the virtual host. Using handlerSSL="true", the default, will force
the protocol to be https. You should also set cookieProps to "https" for SSL-only sites.
Note that while we default checkAddress to "false", this has a negative impact on the
security of your site. Stealing sessions via cookie theft is much easier with this disabled.
-->
<!-- <Sessions lifetime="28800" timeout="3600" relayState="ss:mem" -->
<!-- checkAddress="false" handlerSSL="true" cookieProps="https"> -->
<Sessions lifetime="28800" timeout="3600" relayState="ss:mem"
checkAddress="false" handlerSSL="true" consistentAddress="true"
cookieProps="; path=/; secure; HttpOnly; domain=.99agree.com">
<!--
Configures SSO for a default IdP. To allow for >1 IdP, remove
entityID property and adjust discoveryURL to point to discovery service.
(Set discoveryProtocol to "WAYF" for legacy Shibboleth WAYF support.)
You can also override entityID on /Login query string, or in RequestMap/htaccess.
-->
<SSO entityID="https://shibboleth.nau.edu/idp/shibboleth";>
SAML2
</SSO>
<!-- SAML and local-only logout. -->
<Logout>SAML2 Local</Logout>
<!-- Extension service that generates "approximate" metadata based on SP configuration. -->
<Handler type="MetadataGenerator" Location="/Metadata" signing="false"/>
<!-- Status reporting service. -->
<Handler type="Status" Location="/Status" /> <!-- acl="127.0.0.1 ::1" -->
<!-- Session diagnostic service. -->
<Handler type="Session" Location="/Session" showAttributeValues="true"/>
<!-- JSON feed of discovery information. -->
<Handler type="DiscoveryFeed" Location="/DiscoFeed"/>
</Sessions>
<!--
Allows overriding of error template information/filenames. You can
also add attributes with values that can be plugged into the templates.
-->
<Errors supportContact="root@localhost"
helpLocation="/about.html"
styleSheet="/shibboleth-sp/main.css"/>
<!-- CSU Test IdP metadata -->
<MetadataProvider type="XML" url="https://shibboleth.nau.edu/idp/shibboleth";
backingFilePath="c:\opt\shibboleth-sp\etc\shibboleth\csu-shibidptest-metadata.xml" reloadInterval="3600">
</MetadataProvider>
<!--<MetadataProvider type="XML" file="C:\opt\shibboleth-sp\etc\shibboleth\SP_Metadata_Incommon.xml"/> -->
<!-- Example of locally maintained metadata. -->
<!--
<MetadataProvider type="XML" file="partner-metadata.xml"/>
-->
<!-- Map to extract attributes from SAML assertions. -->
<AttributeExtractor type="XML" validate="true" reloadChanges="false" path="attribute-map.xml"/>
<!-- Use a SAML query if no attributes are supplied during SSO. -->
<AttributeResolver type="Query" subjectMatch="true"/>
<!-- Default filtering policy for recognized attributes, lets other data pass. -->
<AttributeFilter type="XML" validate="true" path="attribute-policy.xml"/>
<!-- Simple file-based resolver for using a single keypair. -->
<CredentialResolver type="File" key="sp-key.pem" certificate="sp-cert.pem"/>
<!--
The default settings can be overridden by creating ApplicationOverride elements (see
the https://wiki.shibboleth.net/confluence/display/SHIB2/NativeSPApplicationOverride topic).
Resource requests are mapped by web server commands, or the RequestMapper, to an
applicationId setting.
Example of a second application (for a second vhost) that has a different entityID.
Resources on the vhost would map to an applicationId of "admin":
-->
<!--
<ApplicationOverride id="admin" entityID="https://admin.example.org/shibboleth"/>
-->
</ApplicationDefaults>
<!-- Policies that determine how to process and authenticate runtime messages. -->
<SecurityPolicyProvider type="XML" validate="true" path="security-policy.xml"/>
<!-- Low-level configuration about protocols and bindings available for use. -->
<ProtocolProvider type="XML" validate="true" reloadChanges="false" path="protocols.xml"/>
</SPConfig>
- [Metadata-Support] Reg: Shibboleth Integration Unable to locate metadata for identity provider Issue., PraveenKumar Dokula, 03/19/2019
- Re: [Metadata-Support] Reg: Shibboleth Integration Unable to locate metadata for identity provider Issue., Patrick Radtke, 04/16/2019
Archive powered by MHonArc 2.6.19.