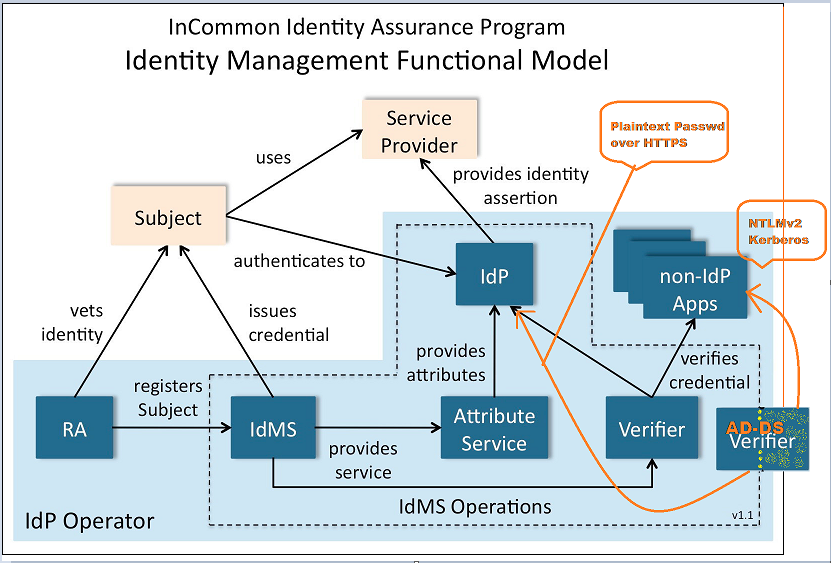
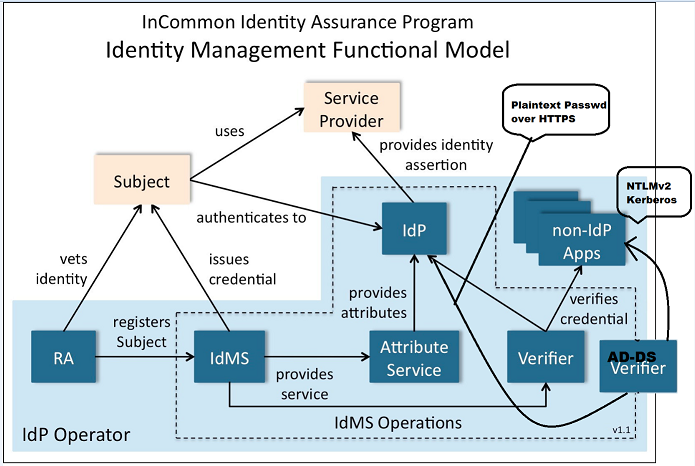
ad-assurance - RE: [AD-Assurance] AD:DS "Split-personality" verifier Diagram
Subject: Meeting the InCommon Assurance profile criteria using Active Directory
List archive
- From: "Capehart,Jeffrey D" <>
- To: "" <>
- Subject: RE: [AD-Assurance] AD:DS "Split-personality" verifier Diagram
- Date: Fri, 6 Dec 2013 16:23:04 +0000
- Accept-language: en-US
|
Sure. I had thought about that, but the color didn’t change the first time I tried, so I used a different technique. I gave a spray-painted graffiti look to the split-off part, and put a dotted line down the
middle.
From: [mailto:]
On Behalf Of Ann West Hi Jeff, A minor suggestion but might be helpful for clarity: can you change the new lines to use a different color? Thanks, Ann On 12/6/13 9:55 AM, "Capehart,Jeffrey D" <> wrote:
|
- [AD-Assurance] AD:DS "Split-personality" verifier Diagram, Capehart,Jeffrey D, 12/06/2013
- Re: [AD-Assurance] AD:DS "Split-personality" verifier Diagram, Ann West, 12/06/2013
- RE: [AD-Assurance] AD:DS "Split-personality" verifier Diagram, Capehart,Jeffrey D, 12/06/2013
- RE: [AD-Assurance] AD:DS "Split-personality" verifier Diagram, Eric Goodman, 12/06/2013
- RE: [AD-Assurance] AD:DS "Split-personality" verifier Diagram, Capehart,Jeffrey D, 12/06/2013
- Re: [AD-Assurance] AD:DS "Split-personality" verifier Diagram, Ann West, 12/06/2013
Archive powered by MHonArc 2.6.16.